Keygaps in Web Wallets
To make a payment in almost any digital cryptographic system you need a private RSA key. Your public key is visible to everybody, but the private key is what makes it possible to make modifications to your wallets. This is exactly how Zold works too. However, remembering those long multi-symbol cryptic texts is a hassle. For micro payments it’s easier to use keygaps.
When you create a Zold wallet, you need a public RSA key. In order
to generate it you use the ssh-keygen
command line tool:
$ ssh-keygen -t rsa -b 4096You will get two files: id_rsa.pub which is small, and is your public key;
and id_rsa which is much bigger, and is your private key. Then you create a wallet:
$ zold create --public-key=id_rsa.pubSee, the private key is not used in this step. Only the public one is
needed to create a wallet, and the key will stay in the wallet for its
lifetime. For example, check out this wallet 00000000000ff1ce.
At the top of the file there is its public RSA key.
Then, when you send a payment, you have to provide your private RSA key, in order to sign a transaction:
$ zold pay --private-key=id_rsa \
00000000000ff1ce 912ecc24b32dbe74 14.95This is how it works from the command line. To make life easier for the majority of our users we created a web wallet at wts.zold.io. There, all these operations are done from the web front end. When you sign up, the system generates the two keys for you, creates a wallet, and pushes the wallet to the network.
The problem we faced during the development of this system was: what should we do with your private key? If we keep it in the database, you might not trust us, since there are two obvious risks: we could steal your money and our database might get hacked. There are plenty of incidents of both kinds in the modern crypto market.
On the other hand, asking you to store the private key locally and provide it to us for every payment is not convenient at all. Because the key is big.
So we found a solution, which we’ve labeled keygaps. We simply take a piece out of the private RSA key and return it to you on sign up: a small string of 8 characters. We remove that string from the RSA key and store the key in the database. Then, when you want to make a payment, we ask you to provide that keygap. Next we inject it into the RSA key from our database, make a payment, and throw the keygap away.
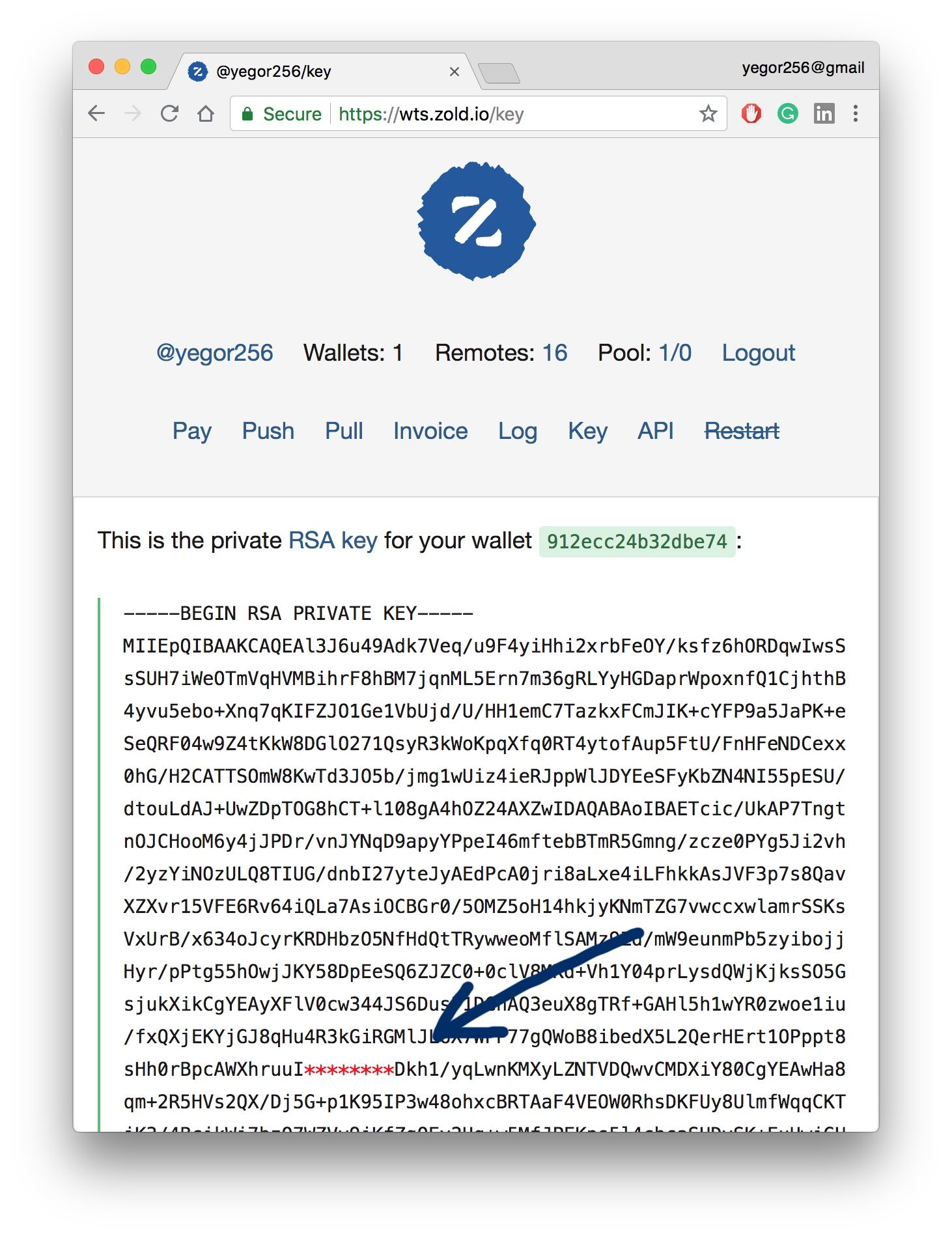
For example, here is my keygap: 5cth9vOt. (I’m kidding.)
Thus we never store your RSA private keys in our database. Even if we get hacked the keys won’t be usable, since each of them will miss a small but very important part.
It’s convenient for a user to keep a small 8-character keygap somewhere secure and never have to worry about that large RSA private key.
Also, if you don’t want to lose your wallet in case our wts.zold.io is down or something else happens to us, you can download the key, inject your keygap into it and use your wallet locally, from the command line.
What about security and the key’s strength? Of course, the keygap is a much weaker protection than the entire RSA key. There are only 628 (218 trillions) possible combinations of it. With a pretty fast computer, in a few months of work, a hacker may find it, if he or she has the RSA key, but doesn’t have the missing keygap. Thus, if 1) you really worry about your ZLD in the wallet, 2) the amount is bigger than the cost of that super computer a hacker will have to use in order to steal your money, and 3) you don’t trust that our database is secure enough, you should just work through our command line tool and never give away your private RSA key, to anybody.
But since Zold is mostly targeted at micropayments, we believe that keygaps will be strong enough for the majority of our users.
